Challenge Name: Windy Day
Category: Forensics
Author: @Skat
Challenge Description:
I have really bad memory. I was analyzing something but then lost track of an important note...
Artifact Files:
- memdump.mem
Because the flag string isn't protected beyond b64, this CTF can be cheesed pretty easily with a one-liner using binary refinery:
emit irisctf | b64 -R | snip :-3 | xargs -I {} grep -m 1 -iE '{}.*\=$' <(strings -e l memdump.mem) | b64But I want to write up a more relevant solution in terms of memory analysis.
For this solution we'll be using volatility 2, but can also be easily accomplished using MemProcFS if you prefer that :)
Step 1: Finding a Valid Profile
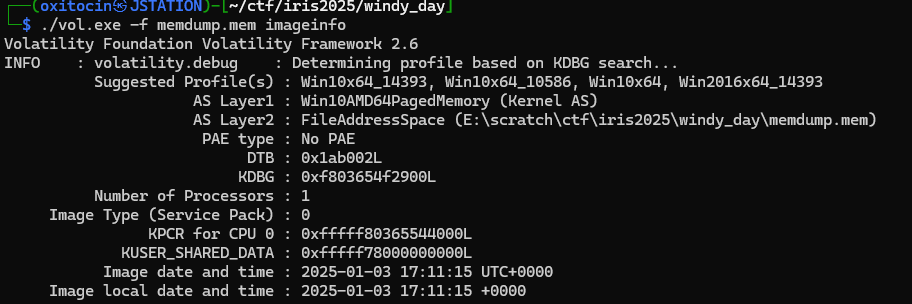
To start, we'll use imageinfo to find a valid profile to pass to volatility when using plugins:
vol.exe -f memdump.mem imageinfoOutput:
Step 2: Analyzing Running Processes
Then I'll look for running processes with pstree, this gives a clean output and shows which parent process we should dump for interesting running processes. I didn't notice any programs open that may be used to take notes down, but we do see firefox - maybe this will be related to searches or website visits:
./vol.exe -f memdump.mem --profile Win10x64_14393 pstreeFirefox output:
0xffffe38cb818b500:firefox.exe 3036 4060 89 0 2025-01-03 16:55:40 UTC+0000
. 0xffffe38cb75b9080:firefox.exe 3968 3036 22 0 2025-01-03 16:55:41 UTC+0000
. 0xffffe38cb7e32680:firefox.exe 7116 3036 19 0 2025-01-03 17:10:01 UTC+0000
. 0xffffe38cb7e25080:firefox.exe 2252 3036 19 0 2025-01-03 17:10:01 UTC+0000
. 0xffffe38cbbc9e080:firefox.exe 2920 3036 19 0 2025-01-03 17:09:56 UTC+0000
. 0xffffe38cbb884800:firefox.exe 6256 3036 19 0 2025-01-03 17:09:56 UTC+0000
. 0xffffe38cbb539800:firefox.exe 3828 3036 17 0 2025-01-03 16:55:43 UTC+0000
. 0xffffe38cbba16080:firefox.exe 2712 3036 19 0 2025-01-03 17:09:56 UTC+0000
. 0xffffe38cbbbe8800:firefox.exe 4508 3036 19 0 2025-01-03 17:09:59 UTC+0000
. 0xffffe38cbbbb8080:firefox.exe 4344 3036 19 0 2025-01-03 17:10:00 UTC+0000
. 0xffffe38cbb380080:firefox.exe 3624 3036 5 0 2025-01-03 16:55:41 UTC+0000
. 0xffffe38cbb7c8800:firefox.exe 5044 3036 5 0 2025-01-03 16:56:43 UTC+0000
. 0xffffe38cbbb44080:firefox.exe 2308 3036 19 0 2025-01-03 17:09:56 UTC+0000
. 0xffffe38cbba94080:firefox.exe 5324 3036 19 0 2025-01-03 17:09:52 UTC+0000
. 0xffffe38cbb89e400:firefox.exe 740 3036 19 0 2025-01-03 17:10:01 UTC+0000
. 0xffffe38cbb8c0800:firefox.exe 5196 3036 19 0 2025-01-03 17:09:56 UTC+0000
. 0xffffe38cbb0d6300:firefox.exe 4772 3036 18 0 2025-01-03 16:57:38 UTC+0000
. 0xffffe38cbb8a9800:firefox.exe 5288 3036 19 0 2025-01-03 17:09:56 UTC+0000
. 0xffffe38cbb261080:firefox.exe 5804 3036 19 0 2025-01-03 17:09:56 UTC+0000
. 0xffffe38cbb116080:firefox.exe 4076 3036 17 0 2025-01-03 16:55:45 UTC+0000
. 0xffffe38cbb711800:firefox.exe 2420 3036 5 0 2025-01-03 16:55:44 UTC+0000
. 0xffffe38cbb8c6800:firefox.exe 3328 3036 19 0 2025-01-03 17:09:56 UTC+0000
. 0xffffe38cbb1e1080:firefox.exe 3132 3036 5 0 2025-01-03 16:55:47 UTC+0000
. 0xffffe38cbbc8c080:firefox.exe 928 3036 19 0 2025-01-03 17:10:00 UTC+0000
. 0xffffe38cbb7c9080:firefox.exe 5664 3036 19 0 2025-01-03 17:09:56 UTC+0000
. 0xffffe38cbbca0080:firefox.exe 3124 3036 19 0 2025-01-03 17:10:01 UTC+0000Step 3: Dumping Memory of Firefox
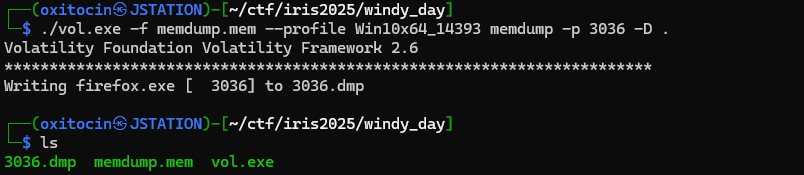
To test our theory, let's dump the memory of the firefox parent process using memdump, and check for interesting strings:
./vol.exe -f memdump.mem --profile Win10x64_14393 memdump -p 3036 -D .Output:
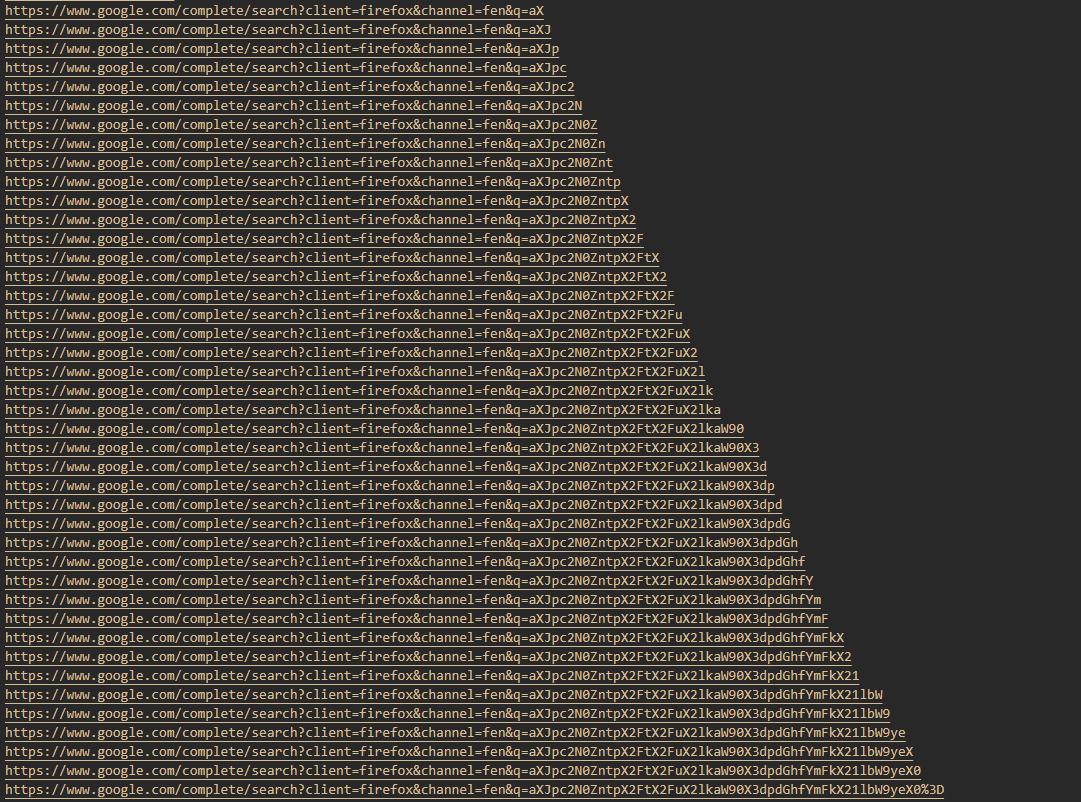
Looking through the strings, I didn't see much interesting http traffic (outside of some datacenter IPs), but saw a lot of https traffic, so I carved those out to a file to look through. We use the -e l flag for strings because these are UTF-16 encoded strings, and a regular strings search wasn't producing proper results:
strings -e l 3036.dmp | grep '^https://' | sort -u > firefox_sites.txtOutput:
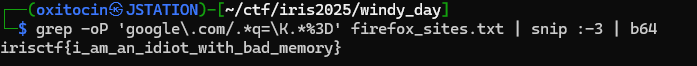
Bingo! We can quickly convert the largest b64 string we see and find the flag:
grep -oP 'google\.com/.*q=\K.*%3D' firefox_sites.txt | snip :-3 | b64Output:
Flag:
irisctf{i_am_an_idiot_with_bad_memory}
Additional Findings:
Couple of Easter Eggs / Additional findings below :)
- Trojan malware being analyzed was
fee.exefrom GitHub - Not sure if
fee.exewas saved asrickroll.exeinUsers\ADMINI~1\DOWNLO~1\rickroll.exe, but that exists ;)
Strings from interesting memory regions which may or may not be related to the malware Skat was checking out:
http://179[.]188.38.42/(some accreditation site related to Araçariguama brazil)destip=42[.]112.25.208;(Vietnam, Fixed line ISP)destip=42[.]0.29.32;(Malaysia, DataCenter)unzip.exe(likely trojan payload)$TROJANPATH = @TEMPDIR & "\" & "$TROJANKEY = "$FULSCPT = FILEOPEN ( $TROJANPATH , 0 )$S_ENCRYPTPASSWORD = "ioiooiioioio"$OPCODE = "0x89C04150535657524889CE4889D7FCB2(trojan-related ps1)office287@gmail.com(??? )info@theadvertiser.biz(??? )RVRmMmQa1EYo(partial base?)aJK0fI8NaUTOUM6NacH5aYdBrIvPNsazb7IUXz2aQa(partial base?)x.batcertutilusagemshtausageU29mdHdhcmVcXE1pY3Jvc29mdFxcV2luZG93c1xcQ3VycmVudFZlcnNpb25cXFJ1bg==(Software\\Microsoft\\Windows\\CurrentVersion\\Run)i do not wantdonatehttp://forum.ru-board.comhttps://money.yandex.ru